Data Loss Prevention System (DLP)
Data Loss Prevention (DLP) System aims at detecting and alerting users if sensitive information is not protected properly to avoid data leakage and loss owing to human errors. It will monitor the major channels through which data and information are transferred to check whether the data are properly protected and generate alerts to users if the defined protection policy is NOT complied with.
Monitored Channels and How DLP System Works
| Monitored Channels | Channel Details |
| 1. Endpoint Web | Transfer data via Web applications on Staff PC (e.g. WebMail, WebDrive, browser upload, etc.) |
| 2. Endpoint E-mail | Sending e-mails using E-mail clients installed on Staff PC (e.g. Outlook Client, Windows Mail client, etc.) |
| 3. Endpoint Printing | Printing files to printer on Staff PC |
| 4. Endpoint Removable Media | Copy files to Removable Media on Staff PC (e.g. USB drive, external Harddisk, DVD, etc.) |
The detection of the DLP system is based on 3 different sources:
1. The files label defined by users
2. PII (Personal Identifiable Information) from fingerprint extracted from Databases managed by ITSC
3. Regular expression of sensitive information (e.g. Pattern of HKID Card number, Credit Card Number, etc)
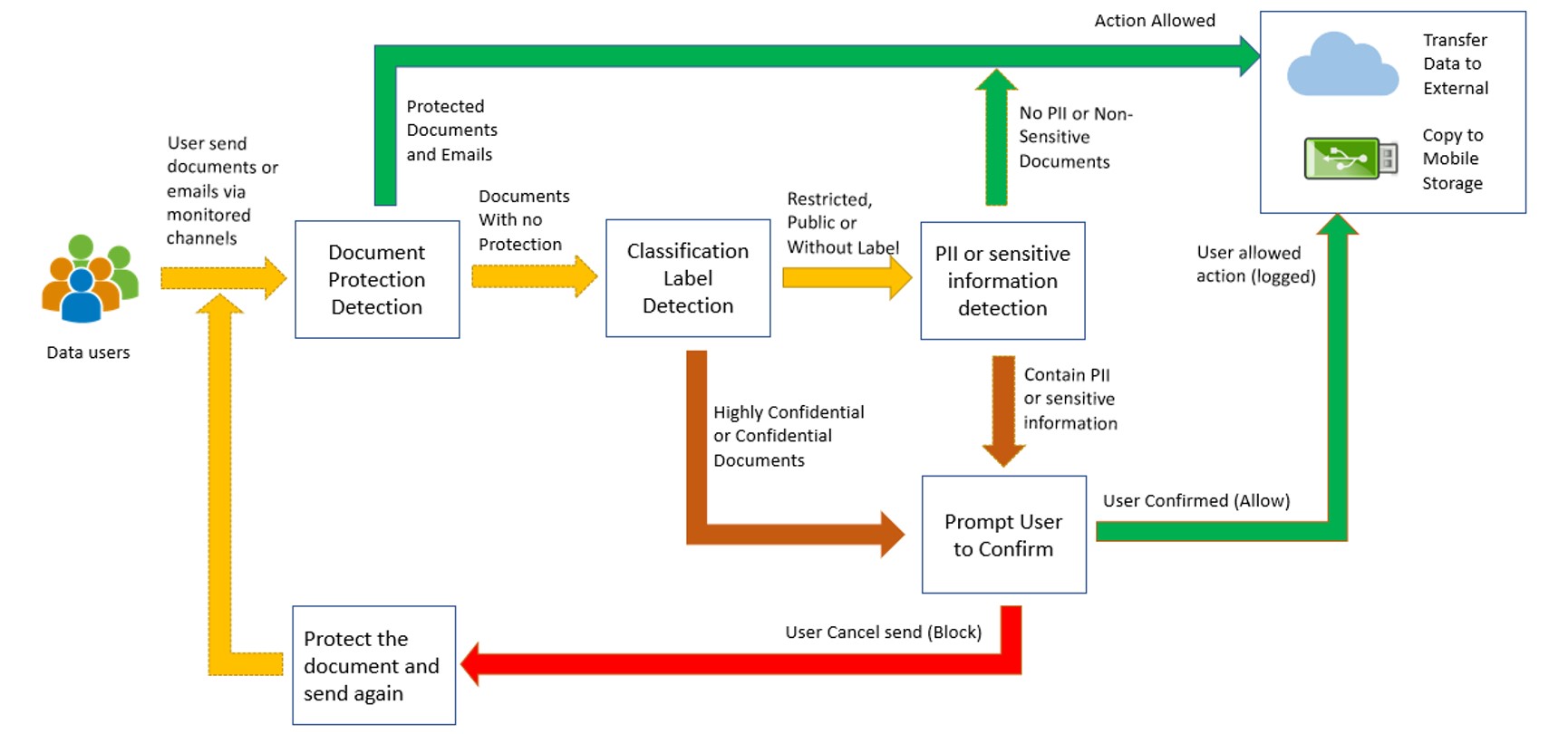
Fig 1: Detection Process in DLP System
Protect Sensitive and Confidential data
Files and documents classified as “Confidential” or “Highly Confidential” or containing PII shall be password-protected or encrypted before sending out by e-mails, transferring to a mobile device, coping to removable storage, uploading to the web or transferring to external parties via electronic media.
Although the DLP system has been configured to detect PII and sensitive data, the detection is not 100% accurate. In order to better protect the University’s data, users are reminded to do the following when processing data:
• Label all files and emails with a correct classification
• Double check the information is being sent to the correct parties
• Think twice if the copying of Sensitive Data to mobile devices or removable media is necessary. Other alternatives such as OneDrive, SharePoint, Teams, etc. that serve the same purpose can be considered (Those systems have built-in access rights and password controls)
• Make sure you handle all sensitive and confidential data with extreme caution and meet the requirements as described in the Information Security Policy
• Make sure you comply with the requirements stated in the “Code of Practice for Handling Personal Data” and “Personal Data (Privacy) Ordinance” when handling or transferring personal data.
User Guides

